Simple account takeover
Photo by Max Bender on UnsplashI wanted to share a simple account takeover technique and the common pattern I found when it was available. Now there aren’t that many websites that expose this anymore as they seem to care more about personal information yet it is still out there.Account enumerationIf you are here you probably know what that is but in case you don’t I will paste the first google definition I got since it seems to be very accurate:“Account enumeration is a common vulnerability that allows an attacker who has acquired a list of valid usernames, IDs, or email addresses to verify whether or not a user exists in a system.”So a vulnerable site will look something like this:This is a message I got in a registration form. It tells me that email is already used (I used it earlier myself) so let’s see what we can do.Bypassing the errorYou might be thinking: Ok, so you know what email is registered on that website, What is the big deal about that?Well, not only this is a bad practi

I wanted to share a simple account takeover technique and the common pattern I found when it was available. Now there aren’t that many websites that expose this anymore as they seem to care more about personal information yet it is still out there.
Account enumeration
If you are here you probably know what that is but in case you don’t I will paste the first google definition I got since it seems to be very accurate:
“Account enumeration is a common vulnerability that allows an attacker who has acquired a list of valid usernames, IDs, or email addresses to verify whether or not a user exists in a system.”
So a vulnerable site will look something like this: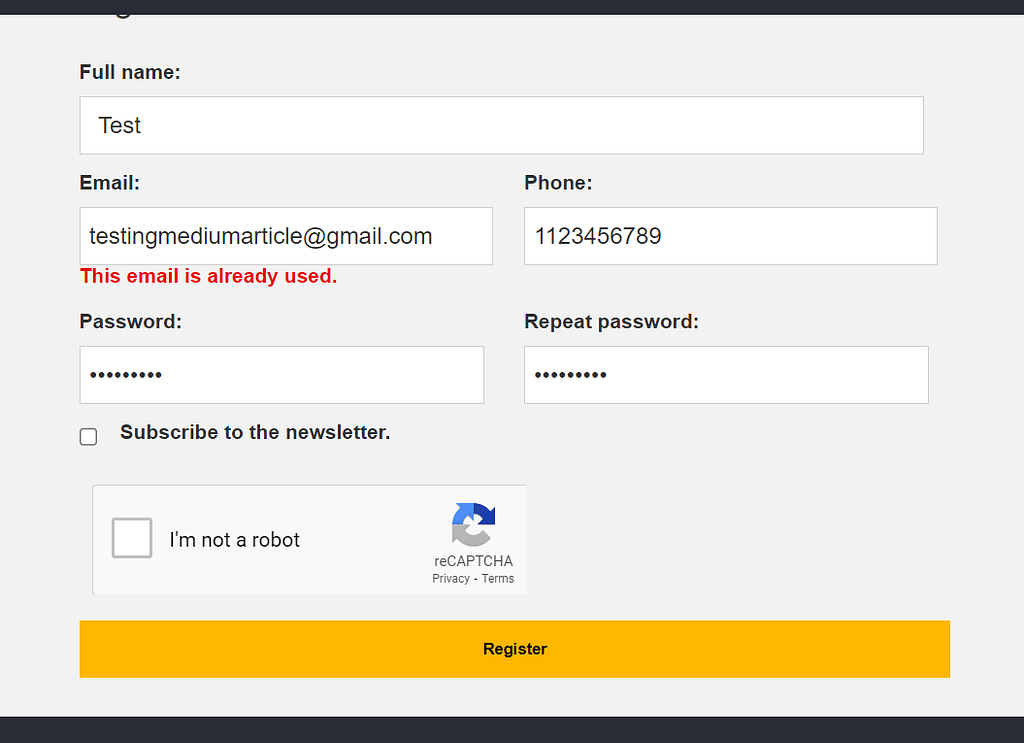
This is a message I got in a registration form. It tells me that email is already used (I used it earlier myself) so let’s see what we can do.
Bypassing the error
You might be thinking: Ok, so you know what email is registered on that website, What is the big deal about that?
Well, not only this is a bad practice when developing a website but I found that sites that had this type of behavior were only doing checks in the front end. This means we have to find a way to bypass that as it doesn’t allow me to re-register with that message active.
You can disable the JavaScript function in the front end and continue but I will do something easier. Instead of [email protected], I will use [email protected] so I don’t trigger the warning and that allows me to press the register button successfully. After that, I will use the proxy in Burp Suite and intercept the traffic: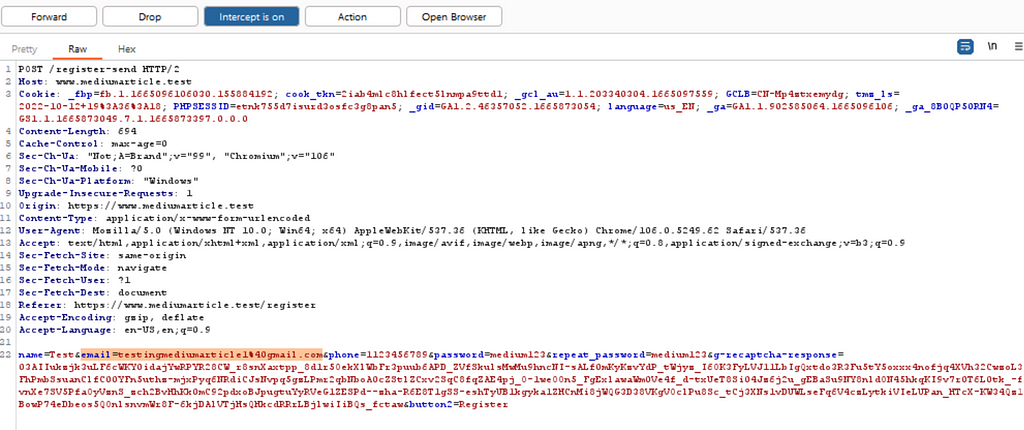
Here you can change back to the original email (I just delete the 1) and forward the traffic. If this is successful there is a chance to have access to the account.
Note that it will be considered an account takeover attack if:
-After registration, the page logs you in immediately or
-The account does not ask you to validate your email before login in.
In the scenario that this works but you still need to validate the email, since you are not supposed to own the email it won’t be as severe as the other two scenarios but it is still, an issue if the system allows you to do that (and it changes the legit user’s password).
What's Your Reaction?





















